A next-generation firewall (NGFW) is a security appliance that processes network traffic and applies rules to block potentially dangerous traffic. NGFWs evolve and expand upon the capabilities of traditional firewalls.
A traditional firewall provides stateful inspection of network traffic. It allows or blocks traffic based on state, port, and protocol, and filters traffic based on administrator-defined rules.
A next-generation firewall (NGFW) does this, and so much more. In addition to access control, NGFWs can block modern threats such as advanced malware and application-layer attacks. According to Gartner's definition, a next-generation firewall must include:
- Standard firewall capabilities like stateful inspection
- Integrated intrusion prevention
- Application awareness and control to see and block risky apps
- Threat intelligence sources
- Upgrade paths to include future information feeds
- Techniques to address evolving security threats

Next-generation firewall specifications vary by provider, but they generally include some combination of the following features:
- Application awareness, or the ability to filter traffic and apply complex rules based on application (rather than just based on port). This is a key feature of next-generation firewalls: They can block traffic from certain applications, as well as maintain greater control over individual applications.
- Deep-packet inspection, which inspects the data contained in packets. Deep-packet inspection is an improvement over traditional firewall technology, which only inspected a packet’s IP header to determine its source and destination.
- Intrusion Prevention System (IPS), which monitors the network for malicious activity and blocks it where it occurs. This monitoring can be signature-based (matching activity to signatures of well-known threats), policy-based (blocking activity that violates security policies), or anomaly-based (monitoring for abnormal behavior).
- High performance, which allows the firewall to monitor large amounts of network traffic without slowdown. Next-generation firewalls include a number of security features that require processing time, so high performance are important to avoid disrupting business operations
- External threat intelligence, or communication with a threat intelligence network to ensure that threat information is up to date and help identify bad actors.
In addition to these foundational features, next-generation firewalls may include additional features such as antivirus and malware protection. They may also be implemented as a Firewall as a Service (FWaaS), a cloud-based service that provides scalability and easier maintenance. With FWaaS, the firewall software is maintained by the service provider, and resources scale automatically to meet processing demand. This frees enterprise IT teams from dealing with the burden of handling patches, upgrades, and sizing.
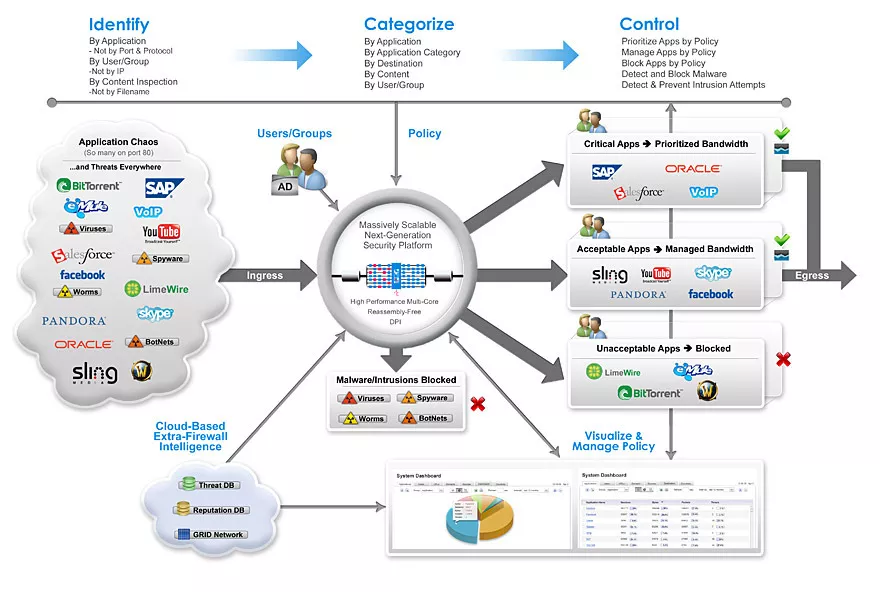
Next-Generation Firewalls (NGFWs) offer a range of benefits that make them a crucial component of modern cybersecurity strategies. Here are some of the key advantages:
- Advanced Threat Protection: NGFWs employ advanced techniques like deep packet inspection, intrusion detection and prevention, and behavioral analysis to detect and block sophisticated threats, including zero-day exploits, malware, and advanced persistent threats (APTs).
- Application Awareness and Control: NGFWs can identify and control applications and services running on the network, allowing organizations to enforce policies based on the specific applications being used. This helps improve security and manage bandwidth effectively.
- User Identity and Access Control: NGFWs integrate with identity management systems, enabling user-specific policies. This means that organizations can control access based on individual user identities, reducing the risk of unauthorized access.
- Content Filtering: NGFWs inspect the content of web traffic, emails, and file transfers for malicious content, inappropriate content, and compliance violations. This feature helps protect against malware infections, data leaks, and access to harmful websites.
- SSL/TLS Inspection: NGFWs can decrypt and inspect SSL/TLS-encrypted traffic, ensuring that threats are not hidden within encrypted sessions. This capability is crucial as encryption becomes more prevalent.
- Behavioral Analysis: Some NGFWs use machine learning and behavioral analysis to detect abnormal network behavior, helping to identify zero-day threats and attacks that lack known signatures.
- Threat Intelligence Integration: NGFWs often incorporate threat intelligence feeds and databases to identify known malicious IP addresses, domains, and URLs. This information helps block or alert on traffic to and from these sources.
- Logging and Reporting: NGFWs generate detailed logs and reports about network traffic and security events. This information is invaluable for incident response, compliance, and auditing purposes.
- Application Layer Filtering: NGFWs can inspect and filter traffic at the application layer of the OSI model, allowing for precise control and security measures related to specific applications and services.
- Deep Packet Inspection (DPI): DPI allows NGFWs to analyze the entire contents of data packets, enabling the detection of advanced threats and vulnerabilities that may be hidden in packet payloads.
Next-generation firewall vs. Traditional firewall
Traditional firewalls rely on port/protocol inspection and blocking to protect enterprise networks at the data link and transport layers (layers 2 and 4 of the OSI model). This static approach was effective in the past, when the IT environment was less dynamic than it is now, and applications could be identified by port. But with the increasing complexity of virtualized networks and more advanced security threats, it’s no longer enough. Next-generation firewalls are smarter: They can filter packets based on application (layer 7 of the OSI model), and even based on behavior, making fine-grained distinctions that are far more effective than the generic methods used by traditional firewalls. They also refer to external data to identify threats. This dynamic, flexible approach allows them to identify and defend against attackers that are much more sophisticated than in the past.

We need a Next-Generation Firewall (NGFW) because it offers advanced security capabilities that are essential for safeguarding your network and data in today's ever-evolving cybersecurity landscape. Traditional firewalls, while useful, often lack the depth and precision required to combat modern threats. NGFWs go beyond basic packet filtering by providing features such as application awareness, user identity management, intrusion detection, and content filtering. They can identify and thwart complex threats like zero-day attacks and advanced malware, ensuring that your network remains secure. Additionally, NGFWs offer insights into application usage, allowing you to optimize bandwidth and enforce strict security policies. By investing in an NGFW, you enhance your organization's ability to detect, prevent, and respond to cyber threats effectively, ultimately reducing the risk of data breaches and network compromises.